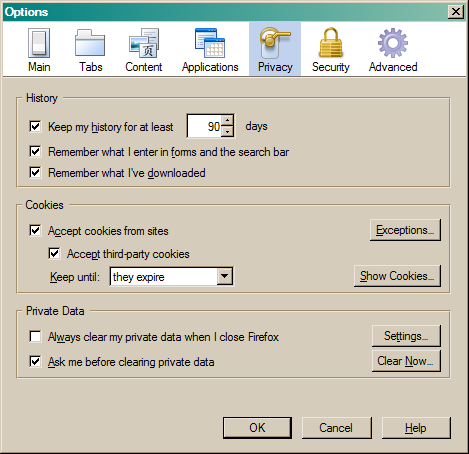
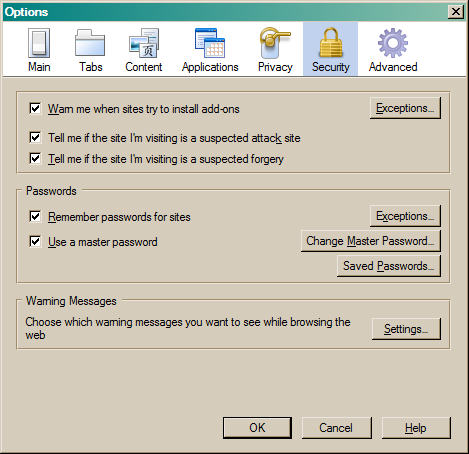
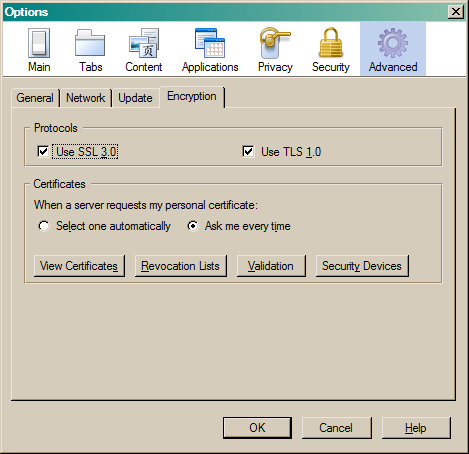
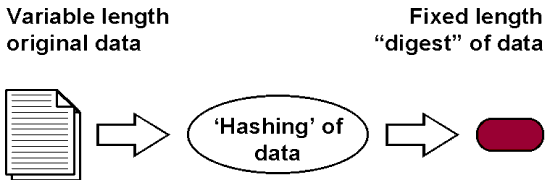
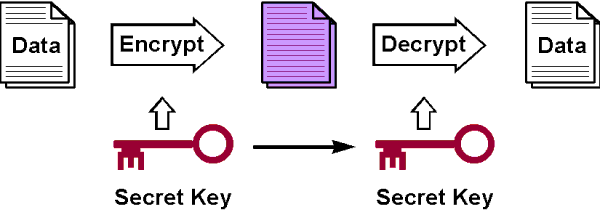
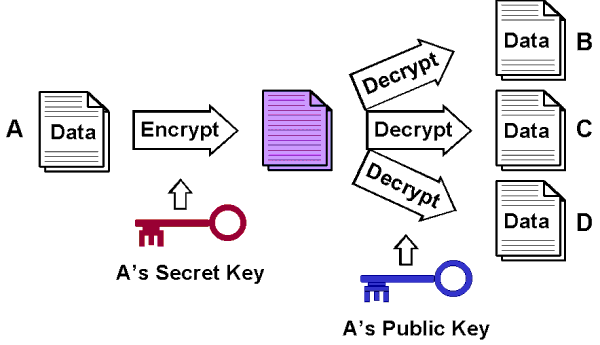
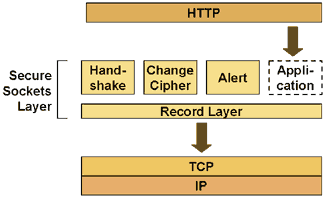
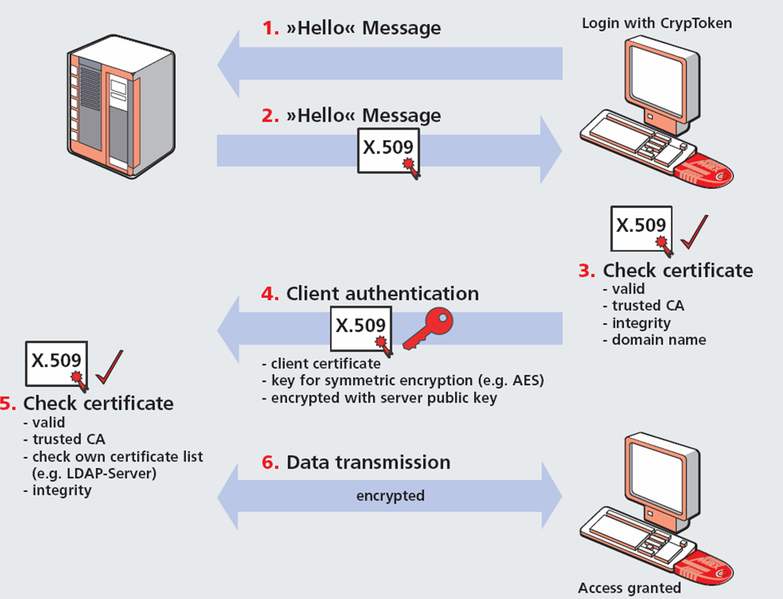
Security & Privacy
Web Architecture [./]
Fall 2011 — INFO 253 (CCN 42598)
Dilan Mahendran, UC Berkeley School of Information
2011-10-18
![]() [http://creativecommons.org/licenses/by/3.0/]
[http://creativecommons.org/licenses/by/3.0/]
This work is licensed under a CC
Attribution 3.0 Unported License [http://creativecommons.org/licenses/by/3.0/]